How to Convert MD5 Passwords to SHA256?
If you are still using MD5 to encrypt passwords in a database, it might be a right move to look for a better algorithm. SHA256 should be a good replacement, and the question today is to see how to migrate from MD5 to SHA256.
As a general rule, MD5 is a hashing function, not an encryption algorithm. It’s not possible to recover MD5 encrypted passwords to store them with another method. So, there is no way to directly convert MD5 hashs to their SHA256 equivalent.
Keep reading, however, as I have some solutions for your problem.
Your essential Linux handbook
Want to level up your Linux skills? Here is the perfect solution to become efficient on Linux. 20% off today!
Download now
Reminder about the MD5 algorithm
As you are asking how to convert MD5 hashs to another format, you probably need a quick reminder before anything else.
About the MD5 function
Enroll in the Complete Cyber Security Course now, and master online safety.
Learn to defeat hackers, protect privacy, and stay anonymous with over 50 hours of on-demand video.
MD5 stands for “Message Digest Algorithm 5”. Many people are confused with the real purpose of the MD5 algorithm, you are not alone.
In fact, it’s not an encryption algorithm, even if many developers use it like this. MD5 is a hashing function.
The only goal of the MD5 function is to convert almost anything (string, number, files) into a short 32 hexadecimal characters string.
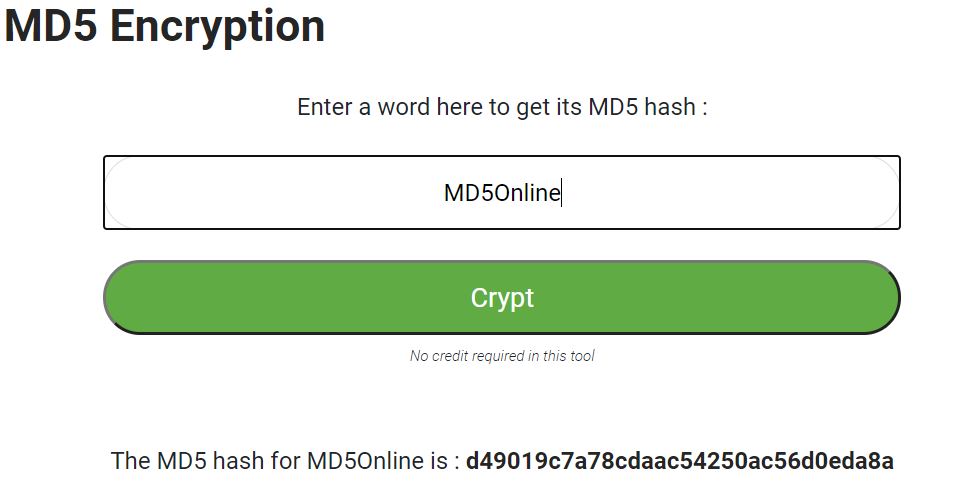
Here is an example: If you apply the MD5 function to the word “MD5Online”, you’ll get “d49019c7a78cdaac54250ac56d0eda8a”.
You can try to hash you own strings with this “encryption” tool on MD5Online.org.
What is the opposite function?
Download your exclusive free PDF containing the most useful Linux commands to elevate your skills!
As you want to convert MD5 strings to SHA256 equivalents, the first idea you might have is to recover the original passwords and then use the SHA256 function to generate a new safer password string.
Well, it doesn’t work like that.
There is no reverse function to the MD5 algorithm. It’s the main difference between an encryption algorithm and a hashing function. With encryption, there is a decryption method available. With hashing, it’s a one-way process, you can’t recover the initial input.
Even with the best tools available to decrypt MD5 hashes, you will never get a 100% success rate to recover your passwords. We currently have around 85% success rate, and if you have a large database, it will take a lot of time to even get this result. So, that’s not the best option.
In the next part, I’ll introduce some better solutions to secure the passwords in your database.
How to convert MD5 to SHA256 in a database
Now that’s the MD5 algorithm is clearer for you, let’s see how to solve your problem.
In fact, I have two solutions for you, depending on your motivations.
Adapt your database
Whatever the solution you choose after that, the first step will be to male sure your database is ready to use SHA256 passwords.
MD5 and SHA256 don’t generate the same data:
- MD5 produces a 32 hexadecimal character string
Example: 098f6bcd4621d373cade4e832627b4f6 - SHA256 generates a longer, 64 characters string
Example: 9f86d081884c7d659a2feaa0c55ad015a3bf4f1b2b0b822cd15d6c15b0f00a08
Let’s suppose you use a VARCHAR(32) for the MD5 password, you’ll need a VARCHAR(64) to store the new value with SHA256.
You could just change the password field type in your table, but I suggest creating a new field in VARCHAR(64) for now.
So, if you are using MySQL as your database engine, it should be something like that:ALTER TABLE myTable ADD new_password VARCHAR(64) NOT NULL AFTER password;
In this case, my MD5 password is in the “password” field, and the SHA256 password will be store in the “new_password” field.
Obviously, adapt this query with the table and fields names corresponding to your environment.
The slow transition: ask users to change their password
Download your exclusive free PDF containing the most useful Linux commands to elevate your skills!
Once the database is ready, the first option is to slowly move from MD5 to SHA256.
As you can’t recover the original passwords from their MD5 hashes, the first idea is to have an intervention from the user, which is the only person to know the original password.
You can either for them to log in, or ask them to change their passwords for security reasons.
When they sign in or change their password, you check the password as usual with the MD5 field, but just after you also store the SHA256 equivalent in the new database field.
Example:
Try it for free now, with advanced security features.
2900+ servers in 65 countries. It's free. Forever.
- The user fill the login form with <user> and <password>
- If MD5(<password>) = password field in the database then
- Update the new_password field with SHA256(<password>)
- Log in
Then you can either wait for all users to log in, or use the SHA256 field once it’s no longer empty for that specific user.
The advantage of this method, is that everything is transparent, but it can take a long transition time before all the users are either logged in or disabled. That’s why I think the second option is better in most cases.
The best solution: convert all passwords to SHA256
To migrate from MD5 to SHA256 to store passwords in a database, the best way is to use the two hashing algorithms in succession. You can apply the SHA256 function to the MD5 password and convert all the store password in one query.
Here is the exact procedure to follow if you are using PHP and MySQL for example:
- Put your website or application in maintenance mode for a few minutes
- Fill the new password field with a SHA256 string:
UPDATE users SET new_password=SHA2(password,256)We add a SHA256 layer above the MD5 value. - Change your website or application to use the new field. For example:
SELECT * FROM users WHERE password=MD5('".$password."')
Becomes:SELECT * FROM users WHERE new_password=SHA2(MD5('".$password."'),256) - Eventually, you can remove the “password” field and rename the “new_password” one to “password”:
ALTER TABLE users DROP password;
ALTER TABLE users CHANGE new_password password VARCHAR(64); - Don’t forget to remove all uses of “new_password” in your application code.
- End the maintenance mode 🙂
That’s it, with this method, you should have a more secure database instantly, and don’t have to ask anything to your users.
Whenever you’re ready for more security, here are things you should think about:
- Break free from Gmail:
You should be able to choose what happens to your data. With Proton, only you can read your emails.
Get private email.
- Protect yourself online:
Use a high-speed Swiss VPN that safeguards your privacy. Open-source, no activity logs.
Get Proton VPN risk-free.
- Master Linux commands:
A sure method to learn (and remember) Linux commands. Useful ones only, one at a time, with clear explanations.
Download the e-book.