Is MD5 Reversible? (Truth, Myths and Solutions)
This is a common question with cryptographic algorithms (MD5, SHA1, etc.). The security issues with these algorithms often come from a misunderstanding of what they are and how they work. In this article, we’ll especially look at the MD5 algorithm and if it can be decrypted or not.
As a general rule, the MD5 algorithm is not reversible, like most hashing functions. It hashes an unlimited set of values into a fixed digest of 32 hexadecimal characters. As several entries can have the same MD5 value, there are no algorithmic way to decrypt it.
Saying the MD5 algorithm is not reversible doesn’t mean it’s the perfect hash function and that there is no way to guess the original value, as we’ll see in this article.
Your essential Linux handbook
Want to level up your Linux skills? Here is the perfect solution to become efficient on Linux. 20% off today!
Download now
Is MD5 Reversible?
Secure your spot in the Accelerator Program, with early access to exclusive resources.
Get 1000+ classes, unlimited mentorship, and more.
If you are reading this article, you probably need a quick reminder on how the MD5 algorithm works. So let’s start with this before seeing solutions to your problem.
How the MD5 algorithm works
MD5 Encryption
The MD5 algorithm is a hashing function. It means that it generates a 32 hexadecimal characters string for any input it takes. You can convert a password, a paragraph or a whole encyclopedia to a MD5 hash from the same length.
For example, applying the MD5 function to the word “MD5Online” gives “d49019c7a78cdaac54250ac56d0eda8a” as a result.
Download your exclusive free PDF containing the most useful Linux commands to elevate your skills!
If you want to learn more on how the MD5 algorithm work, I recommend taking a course about it. I’ll not get into more depth here, but you can find great recommendation on my resources pages.
The myth about MD5 decryption
It’s now common knowledge that the MD5 algorithm has many weak points, and that online websites like MD5Online are pretty good to get the original password from a MD5 hash.
But it doesn’t mean the MD5 algorithm is reversible or that we can decrypt any hash.
There are still some techniques we can use, as we’ll see in the next part.
One of the weaknesses of the MD5 algorithm we can use is that it always gives the same result for the same word.
So, we now know that “d49019c7a78cdaac54250ac56d0eda8a” is the MD5 hash for “MD5Online”.
If we find it somewhere, we can now “decrypt” it. That’s one solution used in our tools, but there are many other options.
Why the MD5 hash function is not reversible
Two MD5 entries can have the same MD5 hash as a result of the hashing function. In this case, there is no way to know which was the original string, even with a database. That’s why we can’t tell that the MD5 hash function is reversible.
In computer science, a collision or clash is a situation that occurs when two distinct pieces of data have the same hash value
Wikipedia
If you want some examples of collision in the MD5 algorithm, you can read this article where I go in more depth about this. Several researchers have proven this concept with both strings and files. So, there is no guarantee that the original entry is the same, even if the MD5 hash is identical.
For those who want the technical answer, you can find on the Wikipedia page that the MD5 algorithm uses the modulo operation in its code. There is no way to reverse a modulo by knowing only the result.
Is there any Way to Decrypt MD5?
As a whole, there is no ultimate solution to decrypt a MD5 hash 100% of the time. But techniques like brute force and database achieve a good success rate against short words hashed with the MD5 algorithm.
Using a Database to Decrypt MD5 hashes
I already introduce the idea behind an MD5 database previously. As any input string will always give the same hash as the result of the MD5 algorithm. We can pre-compile a list of words or strings, and store their MD5 equivalent in a database.
We can then use this database against a list of MD5 hashes, and try to use it to decrypt some values.
Download your exclusive free PDF containing the most useful Linux commands to elevate your skills!
Here is a short example:
a:0cc175b9c0f1b6a831c399e269772661
b:92eb5ffee6ae2fec3ad71c777531578f
c:4a8a08f09d37b73795649038408b5f33
d:8277e0910d750195b448797616e091ad
You can store many words like this. You can create a database sequentially (a….z, aa..zz, etc.) or by hashing common words and passwords instead.
And the bigger the table is, the more likely you are to find the word for any MD5 hash.
You can use it with a basic search function, depending on the technology you use to create and store the values.
On M5Online.org, we have several databases, on several servers, so it’s not possible to find an MD5 hash with a simple CTRL+F, but you get the idea 🙂
Join the Complete Ethical Hacking Course Bundle and step into the world of cybersecurity.
Learn to think like a hacker and protect systems with this comprehensive course.
Using Brute Force against MD5 hashes
The second solution is to use brute force against MD5 hashes. In this case, we don’t store anything in a database.
The MD5 function is fast enough to generate hashes on the fly and compare them with the hash we want to decrypt.
By using powerful computers, it can be really fast to find basic words.
You can learn more about the brute force strategy and the tools I recommend in this article.
Using Online Services to Crack MD5 hashes
Obviously, the previous techniques are mostly for educational purpose. Building a giant database will require a lot of time and resources, and getting decent results with brute force will also be a huge investment.
A better solution to save time and money is to use services available for free online. Here is how to do this in a few seconds on MD5Online:
- Access the MD5 decrypt page by clicking on the link.
- You’ll get a form like this:
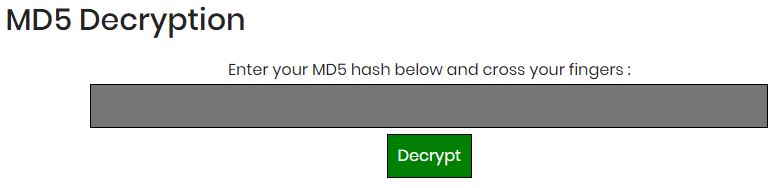
- Enter your MD5 hash in the field and hit “Decrypt”.
As an example, you can use this one: d49019c7a78cdaac54250ac56d0eda8a. - After a few seconds, you’ll get a result, like this one for the sample MD5 hash:
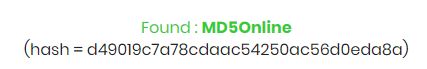
- If there is no result, you can give an email address to receive a notification when the MD5 hash will be decrypted.
It will not work for any word, but with over 1,154 billion words in the database (and growing), there is a big chance that weak passwords will be found. For premium users, we also use other sources and brute force, to get an amazing success rate of 87%.
Whenever you’re ready for more security, here are things you should think about:
- Break free from Gmail:
You should be able to choose what happens to your data. With Proton, only you can read your emails.
Get private email.
- Protect yourself online:
Use a high-speed Swiss VPN that safeguards your privacy. Open-source, no activity logs.
Get Proton VPN risk-free.
- Master Linux commands:
A sure method to learn (and remember) Linux commands. Useful ones only, one at a time, with clear explanations.
Download the e-book.